A while back, our Threat Protection Platform mitigated a Distributed Denial of Service (DDoS) attack targeted at the web site of one of our clients. The attack started at 5 PM UTC and lasted for 5 minutes reaching 25 Gbps, a length frequently observed for this kind of attack but a size over average. The traffic load sourced from around 2500 IP addresses that single targeted one corporate website.
Naturally, the attack never actually reached the client before it was mitigated by our DDoS Threat Protection Platform using our threat insight data.
But let’s take a closer look at how combining the Threat Protection with Threat Insight generates a deeper understanding of the attack.
Threat Insight is a tool that allows you to look up IP addresses and instantly receive a status report on that specific IP. You get insights on the IP’s origin, behavior and history and is also presented comprehensive graphics for easy overview.
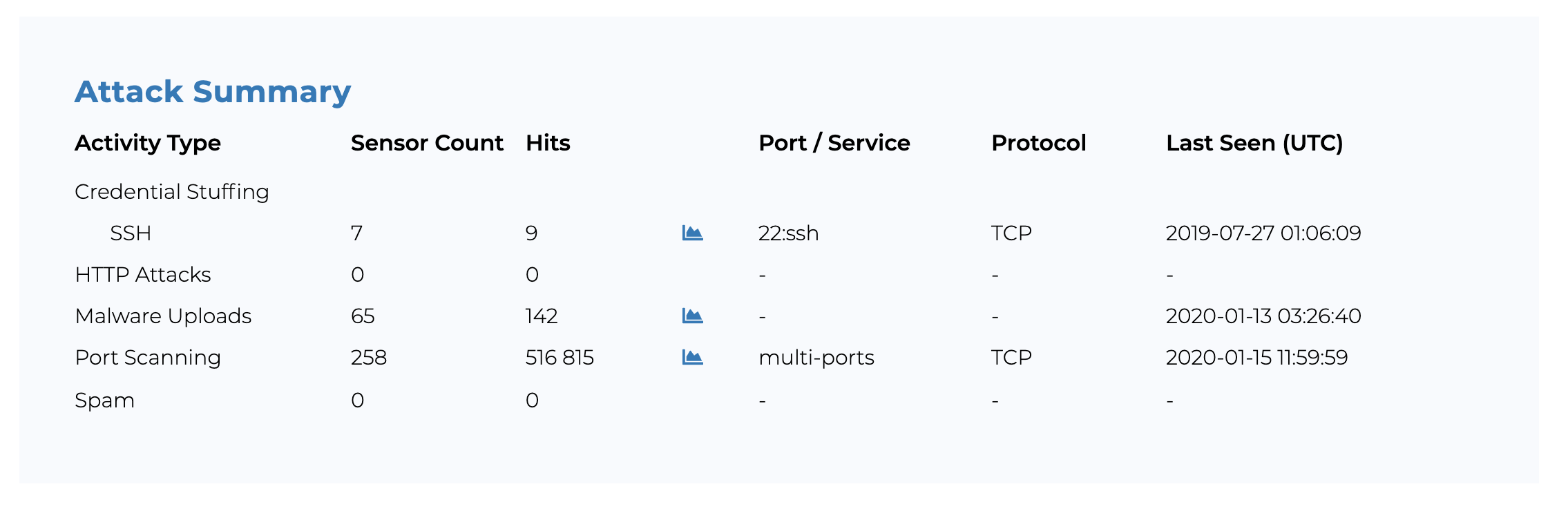
When cross referencing the above mentioned attack into Threat Insight we can conclude that 80% of the IP’s involved in the attack were covered by our threat data. The IP’s, apart from being controlled by a Command & Control server and formerly used in volumetric attacks, had also performed port-scanning and credential stuffing (password guessing), all logged by Baffin Bay Networks global sensory network.
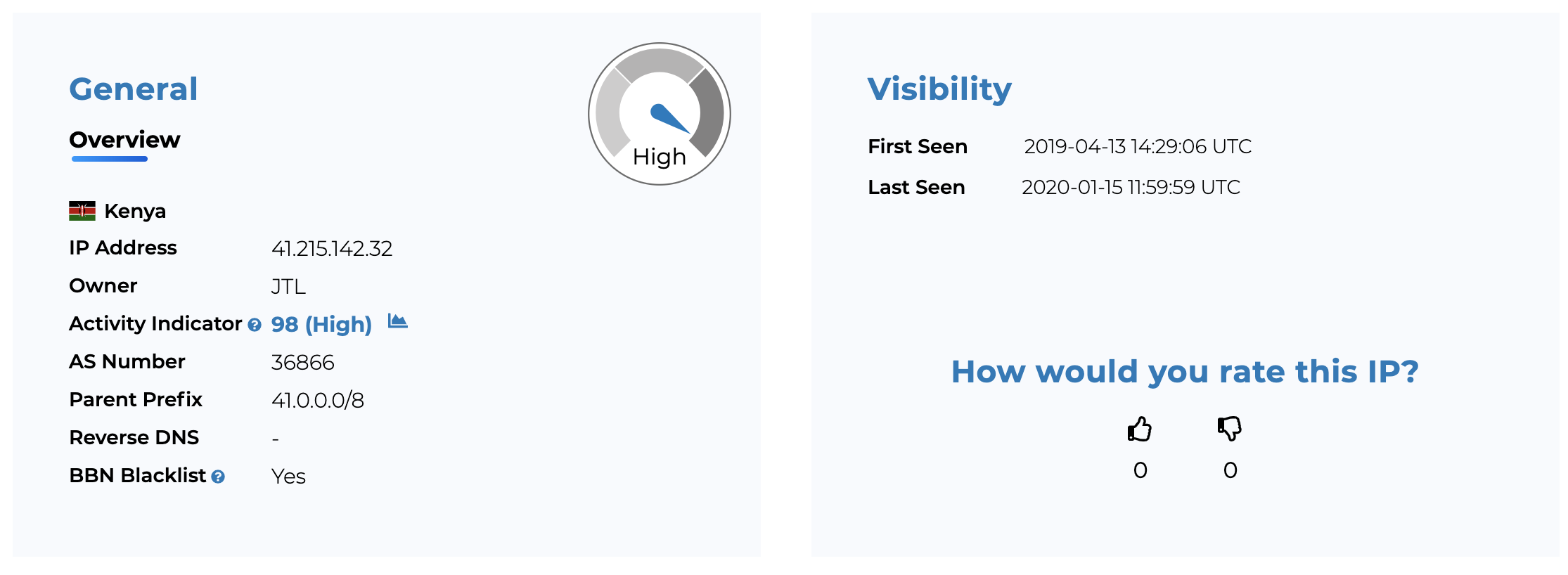
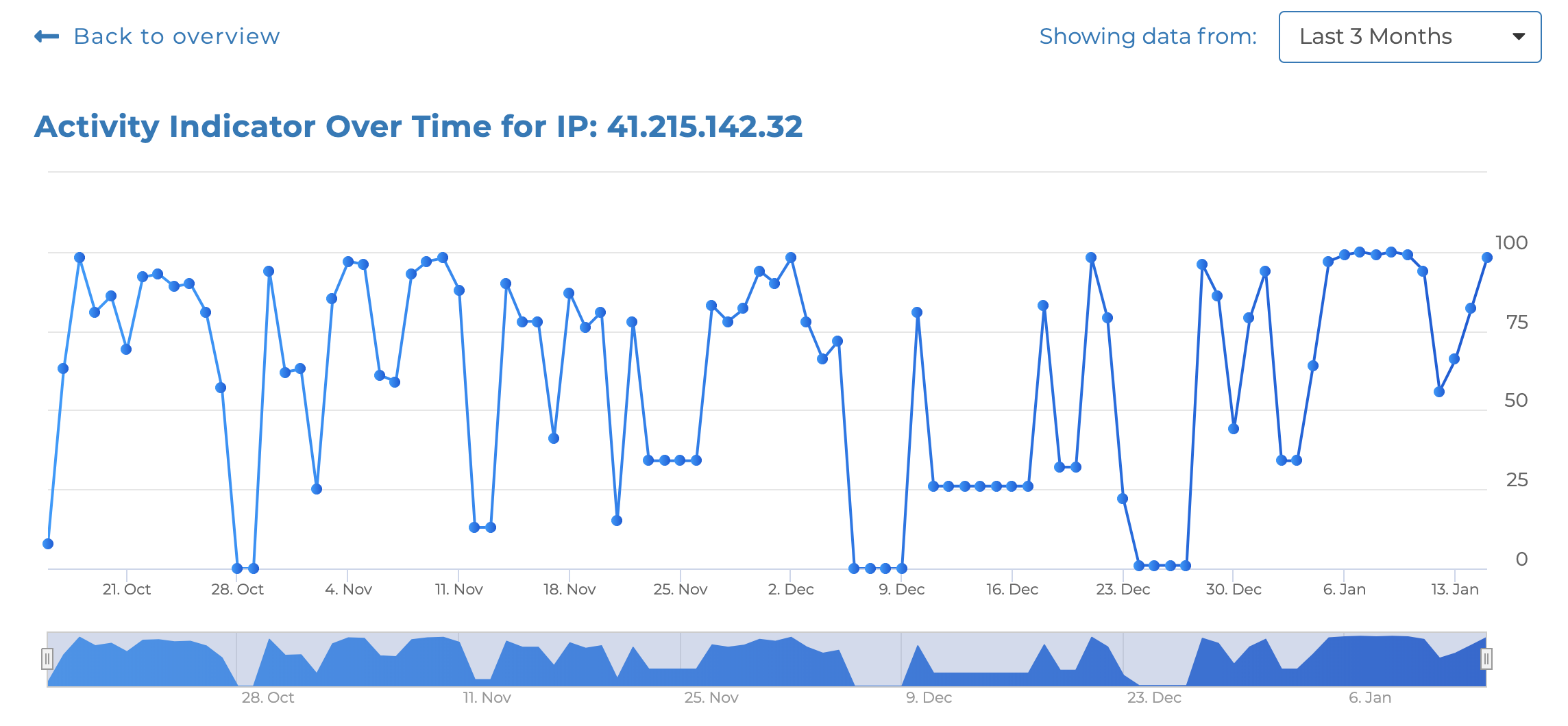
Now let’s dig deeper. When analyzing the IP addresses in the botnet used in the attack, we can quickly locate several high activity IP’s, whereof one we will have a closer look at below. Say hello to 41.215.142.32. This IP is sourced from Kenya and had an activity indicator of 98 at the time of the attack which tells us that the IP has a history of frequent activities. We consider any Activity Indicator above 80 as high. When displaying the graph, we can see that the activities are continuous over time, and when having a closer look at the Attack Summary, we can see that the activities are both credential stuffing and port scanning.
Lastly, you can see that the IP is on the BBN Blacklist, which is why we could mitigate this attack before it got anywhere near our customer’s website.
This kind of insight allows you to not only better understand your threat landscape, but also take proactive action to optimize your own defense. To exemplify. If you often source malicious traffic from a specific country where you neither have a customer base, partners nor suppliers - then you can use your Web Application Firewall to limit traffic from that country. Using Threat Insight will help you understand, act smarter, and even increase cost-efficiency.
Our Threat Data is continuously adapting, evolving and improving because we mitigate these sorts of attacks, and every bit of globally collected data is contributing. This is how we encourage our customers to gain a deeper understanding of the cyber threats that they actually face. This is how we want to contribute to a better and more accurate cyber security community. This is the strength of combining Threat Protection and Threat Insight.
Feel free to contact us if you're interested in a free online demo of our threat protection service, learn more about our services here or try out Threat Insight yourself today.